Identity and Access Management Market Segmentation and Growth Analysis
Identity and Access Management 2024
In an increasingly digital world, the security of information and systems has become paramount for organizations of all sizes. Identity and Access Management (IAM) plays a critical role in protecting sensitive data by ensuring that only authorized individuals have access to specific resources. IAM encompasses a wide range of policies, technologies, and processes aimed at managing digital identities and controlling user access to various systems and data. With the growing concerns over data breaches and cyber threats, the importance of effective IAM strategies cannot be overstated. The Identity and Access Management Market Share has seen significant growth, as businesses recognize the need for robust security measures to protect their digital assets.
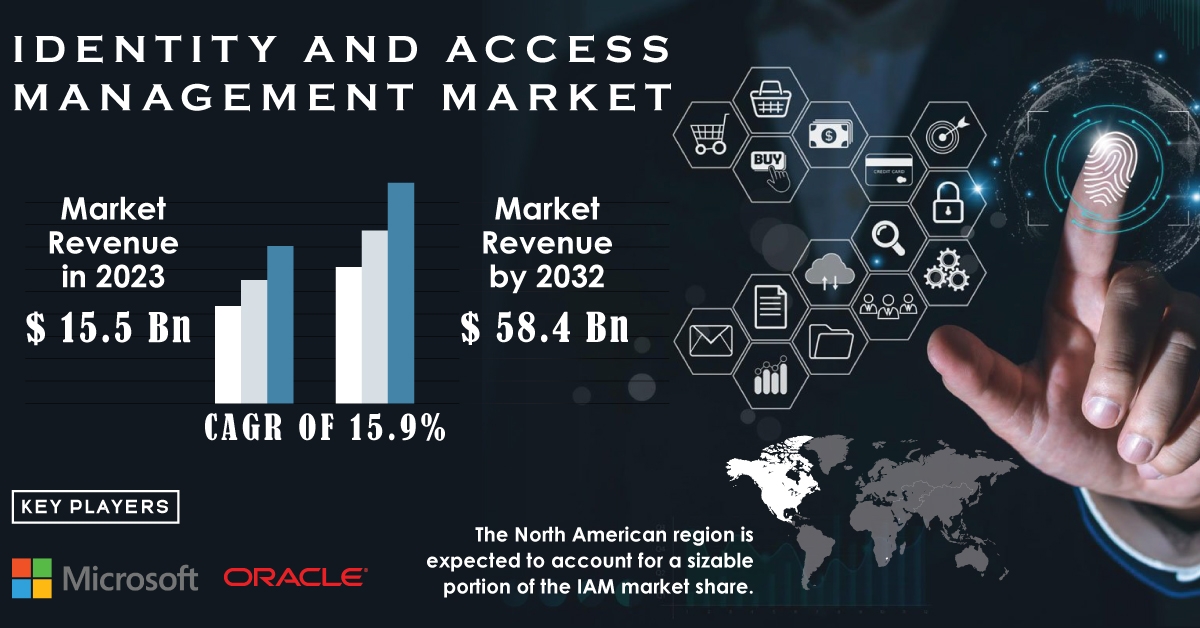
The Identity and Access Management market was valued at USD 15.5 Billion in 2023 and is expected to reach USD 58.4 Billion by 2032, growing at a CAGR of 15.9% over the forecast period from 2024 to 2032. This impressive growth is driven by the increasing adoption of cloud-based solutions, the rise of remote work, and the ever-evolving threat landscape.
What is Identity and Access Management?
At its core, IAM is a framework for ensuring that the right individuals have the appropriate access to technology resources. This involves not only managing user identities but also controlling how those identities are authenticated and what permissions they have within various systems. IAM solutions provide organizations with the tools needed to create, maintain, and revoke user identities, as well as to enforce security policies that govern access to sensitive data.
IAM systems typically include features such as single sign-on (SSO), multi-factor authentication (MFA), user provisioning and de-provisioning, and role-based access control (RBAC). These features work together to streamline the authentication process for users while maintaining a high level of security. By centralizing identity management, organizations can reduce the complexity of managing user access across multiple platforms and applications.
The Importance of IAM in Modern Organizations
The need for IAM solutions has grown exponentially due to the proliferation of digital identities and the corresponding rise in security threats. With remote work becoming the norm and organizations increasingly relying on cloud services, managing access to sensitive data has never been more complex. IAM addresses these challenges by providing organizations with the ability to enforce security policies consistently and efficiently across various systems.
One of the most significant advantages of implementing IAM solutions is improved security. By ensuring that only authorized users can access sensitive data, organizations can reduce the risk of data breaches and unauthorized access. IAM systems can detect and respond to suspicious activities, enabling organizations to take proactive measures to protect their assets.
IAM also enhances operational efficiency. By automating user provisioning and de-provisioning processes, organizations can reduce the time and effort required to manage user access. This efficiency not only saves resources but also minimizes the potential for human error, which can lead to security vulnerabilities.
Furthermore, IAM is essential for regulatory compliance. Many industries are subject to strict data protection regulations that require organizations to implement effective access controls. IAM solutions can help organizations meet these compliance requirements by providing detailed audit trails and reporting capabilities that demonstrate adherence to security policies.
Key Components of IAM Solutions
To effectively manage identities and access, IAM solutions typically consist of several key components. These include identity governance, access management, user provisioning, and directory services.
Identity governance focuses on managing user identities throughout their lifecycle, ensuring that users have the appropriate access based on their roles within the organization. Access management involves controlling how users authenticate to systems and what resources they can access once authenticated. User provisioning automates the process of creating and managing user accounts, while directory services provide a centralized repository for storing and managing user information.
Together, these components create a comprehensive IAM solution that enables organizations to manage identities and access effectively. By integrating these components into a cohesive system, organizations can ensure that their IAM strategies are robust and capable of addressing the challenges posed by modern security threats.
Trends Shaping the Future of IAM
The IAM landscape is continually evolving, driven by advancements in technology and changing security requirements. Several key trends are shaping the future of IAM solutions.
One notable trend is the growing adoption of cloud-based IAM solutions. As organizations migrate their applications and data to the cloud, the need for scalable and flexible IAM solutions that can accommodate this shift has become essential. Cloud-based IAM offers organizations the ability to manage user identities and access from a centralized platform, simplifying administration and improving security.
Another significant trend is the increased focus on user experience. While security is paramount, organizations must also consider the user experience when implementing IAM solutions. Balancing security measures, such as MFA, with seamless user experiences is crucial to ensure that users remain productive while adhering to security protocols. Solutions that offer adaptive authentication and contextual access management are gaining popularity, as they provide a more user-friendly approach to security.
The rise of the Internet of Things (IoT) is also influencing IAM strategies. As more devices become connected to networks, organizations must ensure that they can manage access for these devices effectively. IAM solutions must evolve to accommodate the unique requirements of IoT devices, including the ability to authenticate devices and manage access permissions based on their specific roles.
Challenges in Implementing IAM
Despite the benefits of IAM solutions, organizations may encounter several challenges during implementation. One of the most significant challenges is the complexity of integrating IAM with existing systems and applications. Many organizations have legacy systems that may not support modern IAM solutions, making integration difficult. Organizations must carefully plan their IAM strategy to ensure compatibility with their existing infrastructure.
Another challenge is user resistance to new security protocols. Users may view additional authentication steps, such as MFA, as cumbersome and may resist adopting these measures. Organizations must invest in user education and communication to help employees understand the importance of security and how IAM enhances overall data protection.
Finally, organizations must stay abreast of the rapidly changing threat landscape. Cyber threats are continually evolving, and IAM solutions must adapt to address new vulnerabilities. Regular updates and ongoing training are essential to ensure that IAM strategies remain effective against emerging threats.
Conclusion
Identity and Access Management is an essential component of modern security strategies, enabling organizations to protect sensitive data and manage user access effectively. As the digital landscape continues to evolve, the importance of IAM solutions will only grow. With a projected market value reaching USD 58.4 Billion by 2032, organizations must prioritize IAM as part of their broader security initiatives.
By implementing comprehensive IAM solutions, organizations can enhance their security posture, improve operational efficiency, and ensure compliance with regulatory requirements. Despite the challenges that may arise during implementation, the benefits of a robust IAM strategy far outweigh the risks. In a world where cyber threats are ever-present, investing in effective identity and access management is not just a choice; it is a necessity for organizations seeking to safeguard their digital assets and maintain the trust of their customers.
Contact Us:
Akash Anand – Head of Business Development & Strategy
info@snsinsider.com
Phone: +1-415-230-0044 (US) | +91-7798602273 (IND)
About Us
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Read Our Other Reports:
Digital Forensics Market Share
- Identity_and_Access_Management_Market
- Identity_and_Access_Management_Market_Size
- Identity_and_Access_Management_Market_Share
- Identity_and_Access_Management_Market_Growth
- Identity_and_Access_Management_Market_Trends
- Identity_and_Access_Management_Market_Report
- Identity_and_Access_Management_Market_Analysis
- Identity_and_Access_Management_Market_Forecast
- Identity_and_Access_Management_Industry
- Identity_and_Access_Management_Market_Research
- Industry
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Games
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness
- News


