Data-Centric Security Market Trends, Regional Analysis
Data-Centric Security 2024
Data-centric security is a modern approach to safeguarding sensitive information by prioritizing the protection of the data itself. Unlike traditional security measures that focus on securing the perimeter or infrastructure, data-centric security places the data at the center of the protection strategy. This approach ensures that data remains secure regardless of its location, whether it is stored on-premises, in the cloud, or in transit.
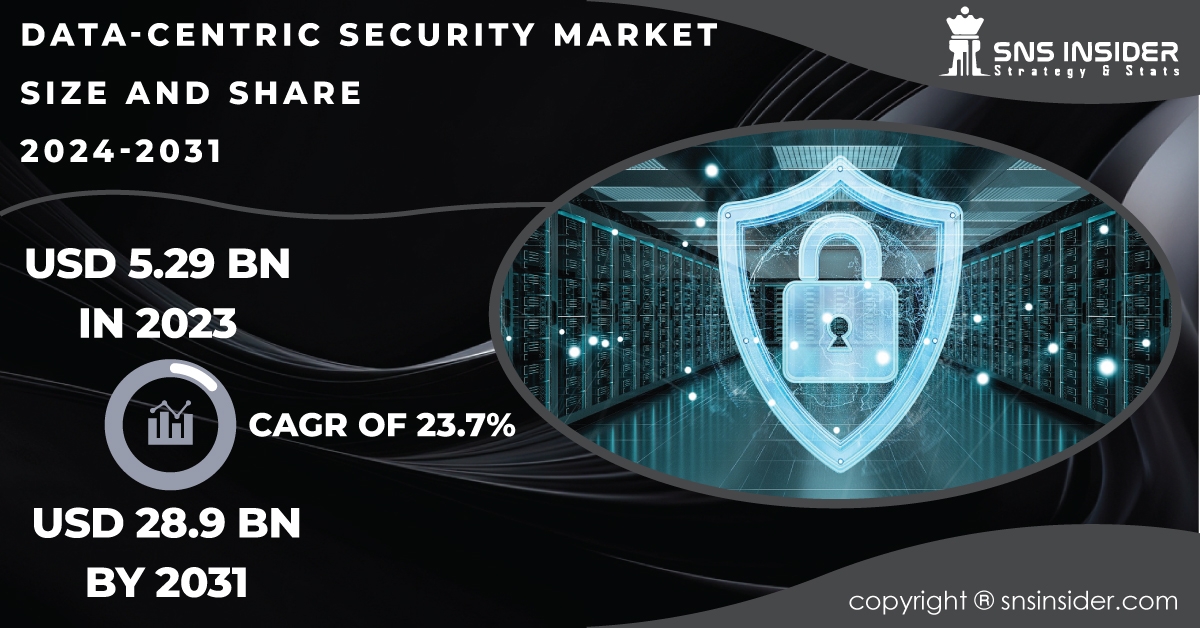
Data-Centric Security Market Size was valued at USD 5.29 Billion in 2023 and is expected to reach USD 28.9 Billion by 2031 and grow at a CAGR of 23.7% over the forecast period 2024-2031.
The rapid growth in the Data-Centric Security market reflects the increasing importance of protecting data in an era of frequent and sophisticated cyber threats. Organizations are recognizing the need for comprehensive data protection strategies that address both internal and external risks, leading to a surge in the adoption of data-centric security solutions.
Essential Elements of Data-Centric Security
-
Encryption Technologies: Encryption is a key component of data-centric security, ensuring that data is transformed into an unreadable format that can only be accessed with the correct decryption key. This technique protects data both at rest and in transit, making it a fundamental element of any data protection strategy.
-
Tokenization and Data Masking: Tokenization replaces sensitive data with unique tokens that have no intrinsic value, while data masking hides sensitive information within a dataset. Both techniques help reduce the risk of data exposure and ensure that sensitive information remains protected in various environments.
-
Access Controls and Identity Management: Implementing strict access controls and identity management practices ensures that only authorized users can access sensitive data. This includes role-based access control (RBAC), attribute-based access control (ABAC), and multi-factor authentication (MFA) to enhance security and minimize unauthorized access.
-
Data Loss Prevention (DLP): DLP solutions monitor and protect data from unauthorized access, leakage, or misuse. These tools help organizations enforce data protection policies, detect potential threats, and prevent data loss by identifying and blocking risky activities.
-
Comprehensive Auditing and Monitoring: Continuous auditing and monitoring of data access and usage are essential for detecting and responding to potential security incidents. This involves logging access events, analyzing patterns, and using automated tools to identify anomalies and potential threats.
-
Data Classification and Labeling: Data classification and labeling involve categorizing data based on its sensitivity and importance. This process helps organizations apply appropriate security measures and manage data according to its classification, ensuring that sensitive information receives the highest level of protection.
Advantages of Data-Centric Security
-
Focused Protection: Data-centric security provides targeted protection by securing the data itself, regardless of where it is stored or how it is transmitted. This approach offers a higher level of protection against data breaches and unauthorized access.
-
Mitigation of Data Breaches: By implementing encryption, tokenization, and other protective measures, organizations can significantly reduce the risk of data breaches. Even if data is compromised, these measures ensure that it remains inaccessible without the appropriate keys or tokens.
-
Regulatory Compliance: Data-centric security helps organizations meet regulatory requirements for data protection, such as GDPR, HIPAA, and CCPA. Ensuring compliance with these regulations is essential for avoiding legal penalties and maintaining trust with customers.
-
Enhanced Data Management: Adopting data-centric security practices improves overall data management by providing better control over data access and usage. This leads to more efficient handling of sensitive information and reduces the risk of accidental or intentional data exposure.
-
Increased Customer Trust: Organizations that prioritize data-centric security demonstrate a commitment to protecting sensitive information, which builds trust with customers and stakeholders. This trust is crucial for maintaining positive relationships and ensuring customer loyalty.
Challenges and Considerations
-
Complex Implementation: Implementing data-centric security solutions can be complex and require significant planning and resources. Organizations must carefully design and execute their security strategies to ensure effective protection without disrupting operations.
-
Cost of Solutions: The cost of data-centric security solutions, such as encryption and tokenization, can be substantial. Organizations need to weigh the benefits of these solutions against their costs and consider long-term investments in data protection.
-
Integration with Existing Systems: Integrating data-centric security measures with existing IT infrastructure and systems can present challenges. Organizations must ensure compatibility and address any potential conflicts or disruptions during the integration process.
-
Adapting to Evolving Threats: The threat landscape is constantly changing, and data-centric security solutions must adapt to address new and emerging risks. Organizations need to stay informed about the latest security trends and technologies to maintain effective protection.
Future Prospects
The future of data-centric security looks promising as technological advancements continue to drive innovation in data protection. Emerging technologies, such as artificial intelligence and blockchain, are expected to enhance data security capabilities and address new challenges. As the market for data-centric security solutions grows, organizations will continue to invest in strategies that ensure the safety and integrity of their most valuable asset: their data.
Conclusion
Data-centric security is a vital approach to protecting sensitive information in the modern digital era. By focusing on the data itself and implementing robust security measures, organizations can safeguard their data from various threats and ensure compliance with regulatory requirements. As the Data-Centric Security market continues to expand, the adoption of effective data protection strategies will play a crucial role in enhancing overall security and mitigating risks in an increasingly interconnected world.
Contact Us:
Akash Anand – Head of Business Development & Strategy
info@snsinsider.com
Phone: +1-415-230-0044 (US) | +91-7798602273 (IND)
About Us
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Read Our Other Reports:
Network Security Firewall Market Trends
- Data-Centric_Security_Market
- Data-Centric_Security_Market_Size
- Data-Centric_Security_Market_Share
- Data-Centric_Security_Market_Growth
- Data-Centric_Security_Market_Trends
- Data-Centric_Security_Market_Report
- Data-Centric_Security_Market_Forecast
- Data-Centric_Security_Market_Analysis
- Data-Centric_Security_Industry
- Industry
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Παιχνίδια
- Gardening
- Health
- Κεντρική Σελίδα
- Literature
- Music
- Networking
- άλλο
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness
- News


